工单节点使用指南 请用平和的语言准确描述你所遇到的问题 厂商的技术支持和你一样也是有喜怒哀乐的普通人类,尊重是相互的 如果是关于 V2EX 本身的问题反馈,请使用 反馈 节点
IP: 104.27.191.245
现在被劫持到菠菜了,根据朋友反馈,影响范围挺大
$ whois 104.27.191.245 % IANA WHOIS server % for more information on IANA, visit http://www.iana.org % This query returned 1 object refer: whois.arin.net inetnum: 104.0.0.0 - 104.255.255.255 organisation: ARIN status: ALLOCATED whois: whois.arin.net changed: 2011-02 source: IANA # whois.arin.net NetRange: 104.16.0.0 - 104.31.255.255 CIDR: 104.16.0.0/12 NetName: CLOUDFLARENET NetHandle: NET-104-16-0-0-1 Parent: NET104 (NET-104-0-0-0-0) NetType: Direct Assignment OriginAS: AS13335 Organization: Cloudflare, Inc. (CLOUD14) RegDate: 2014-03-28 Updated: 2017-02-17 Comment: All Cloudflare abuse reporting can be done via https://www.cloudflare.com/abuse Ref: https://rdap.arin.net/registry/ip/104.16.0.0 OrgName: Cloudflare, Inc. OrgId: CLOUD14 Address: 101 Townsend Street City: San Francisco StateProv: CA PostalCode: 94107 Country: US RegDate: 2010-07-09 Updated: 2018-10-10 Comment: All Cloudflare abuse reporting can be done via https://www.cloudflare.com/abuse Ref: https://rdap.arin.net/registry/entity/CLOUD14 OrgTechHandle: ADMIN2521-ARIN OrgTechName: Admin OrgTechPhone: +1-650-319-8930 OrgTechEmail: [email protected] OrgTechRef: https://rdap.arin.net/registry/entity/ADMIN2521-ARIN OrgNOCHandle: NOC11962-ARIN OrgNOCName: NOC OrgNOCPhone: +1-650-319-8930 OrgNOCEmail: [email protected] OrgNOCRef: https://rdap.arin.net/registry/entity/NOC11962-ARIN OrgAbuseHandle: ABUSE2916-ARIN OrgAbuseName: Abuse OrgAbusePhone: +1-650-319-8930 OrgAbuseEmail: [email protected] OrgAbuseRef: https://rdap.arin.net/registry/entity/ABUSE2916-ARIN RTechHandle: ADMIN2521-ARIN RTechName: Admin RTechPhone: +1-650-319-8930 RTechEmail: [email protected] RTechRef: https://rdap.arin.net/registry/entity/ADMIN2521-ARIN RNOCHandle: NOC11962-ARIN RNOCName: NOC RNOCPhone: +1-650-319-8930 RNOCEmail: [email protected] RNOCRef: https://rdap.arin.net/registry/entity/NOC11962-ARIN RAbuseHandle: ABUSE2916-ARIN RAbuseName: Abuse RAbusePhone: +1-650-319-8930 RAbuseEmail: [email protected] RAbuseRef: https://rdap.arin.net/registry/entity/ABUSE2916-ARIN 22 条回复 2019-06-11 16:00:52 +08:00
1 miyuki 2019-06-08 21:16:47 +08:00 http://104.27.175.71 https://104.27.175.71 http://104.27.191.245 https://104.27.191.245 稳定复现 |
2 Cipool 2019-06-08 21:23:07 +08:00 via Android 好奇什么原理,看路由是正常的 |
4 chenoe 2019-06-08 21:42:08 +08:00 via iPad 江移动无响应,新加坡 HTTP 403 |
5 Myprincess 2019-06-08 22:27:13 +08:00 如果是在某云的话,赶紧学习去,我刚刚学习回来,那个 HOLD 住不能解封。如果你细看现在规则。你会把域名转出去的。站长与快 BO 同罪。 |
6 rushssss 2019-06-08 23:09:38 +08:00 @miyuki 无法复现 http 访问 403: Direct IP access not allowed,https 访问 tls 握手错误: no common encryption algorithm(s). Error code: SSL_ERROR_NO_CYPHER_OVERLAP |
7 zuikren 2019-06-08 23:14:10 +08:00 via Android 国内成功复现,挂代理后无法复现,这个劫持什么原理? |
8 run2 2019-06-09 11:42:30 +08:00 四川电信用户 复现 |
9 johnkiller 2019-06-09 13:33:29 +08:00 湖北联通成功复现 |
10 TechCiel 2019-06-09 14:28:20 +08:00 吉林电信 复现 注意尝试的时候走国内网络 |
11 learningman 2019-06-09 16:44:42 +08:00 江西移动稳定复现 https 是 localhost 签发的什么鬼。。。不应该是 CloudFlare Sni SSL 啥的吗 |
12 txydhr 2019-06-09 18:05:29 +08:00 via iPhone 江苏电信 被劫持 |
13 txydhr 2019-06-09 18:07:13 +08:00 via iPhone 江苏移动 4G 被劫持 |
14 cncmmdwl 2019-06-09 20:58:38 +08:00 福建电信被劫持,啥原理? |
15 wdlth 2019-06-09 21:13:13 +08:00 实现了真正的 AnyCast …… |
16 gerardyang 2019-06-09 21:25:42 +08:00 广东电信成功复现,广东联通成功复现 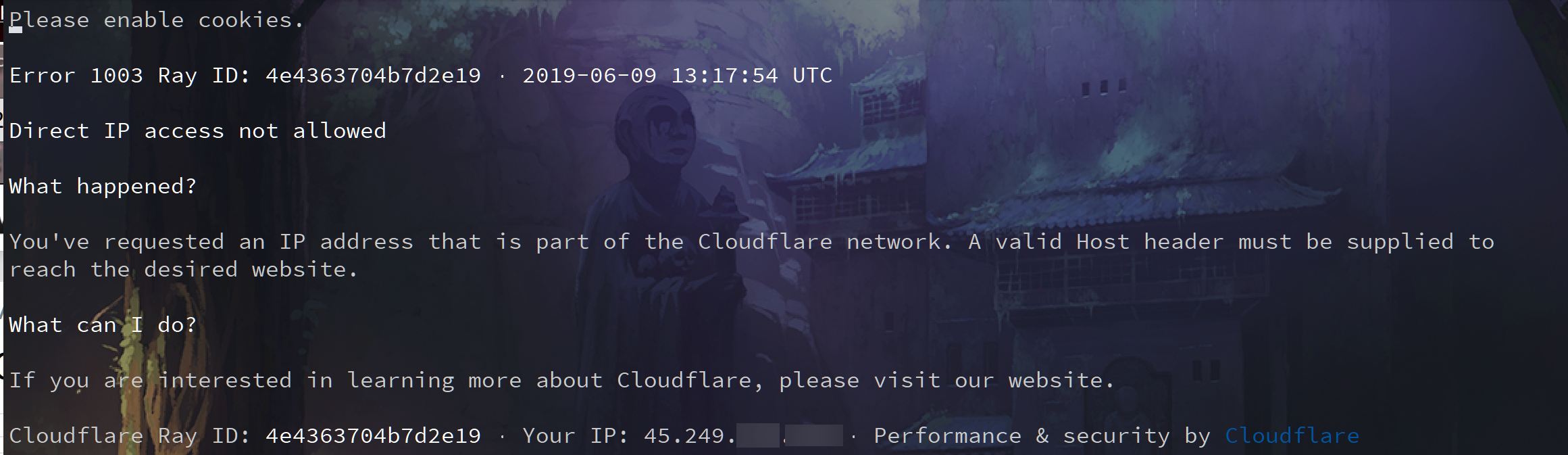 香港 vps 用 w3m 访问 |
17 gerardyang 2019-06-09 21:31:02 +08:00 附上 VPS curl 出来的 https://pastebin.com/c1tt3fbX |
18 chenoe 2019-06-09 22:34:03 +08:00 via Android 浙江移动 1 无响应 浙江移动 2,http 无响应,https 只能加载到 localhost 的证书错误然后无响应 江苏移动成功复现(跳转 x 网) 新加坡、法国 HTTP 403 FORBIDDEN 这是什么鬼。。。国外 IP 自动 ban 的见过,国内还带分区划响应的?还是运营商的机房屏蔽了连接?(两个浙江移动是省内不同的机房和网络) |
19 zhhww57 2019-06-10 00:46:16 +08:00 江苏移动成功复现 |
20 zhhww57 2019-06-10 00:46:31 +08:00 是宽带 |
21 tankren 2019-06-10 09:33:35 +08:00 扑克游戏? |
22 zanzhz1101 2019-06-11 16:00:52 +08:00 山东电信成功复现 |
