OpenWrt 是一个专门面向嵌入式设备的 Linux 发行版。你可以将 OpenWrt 支持的型号的嵌入式设备,比如各种路由器上的系统,换成一个有更多可能性可以折腾的 Linux 系统。 OpenWrt 官方网站
这是一个创建于 220 天前的主题,其中的信息可能已经有所发展或是发生改变。
配置
A 设备 IP 为 10.115.15.1 ,安装 tailscale ,启用--advice-router=10.115.15.0/24
B 设备 IP 为 10.115.15.25 ,安装 tailscale ,不启用--accept-router
C 设备不在局域网 10.115.15.0/24 中,安装 tailscale ,启用--accept-router
存在的问题:
- 10.115.15.0/24 中的设备,可以通过 10.115.15.25 访问到 B 设备
- C 设备,无法通过 10.115.15.25 访问,只能通过 100.0.0.0/8 访问
如果 B 设备 IP 为 10.115.15.25 启用了--accept-router ,10.115.15.0/24 中的设备不能通过 10.115.15.25 访问
需求
不在 10.115.15.0/24 的设备,启用了--accept-router 的设备,可以通过 10.115.15.25 访问该设备
HELP ! HELP ! HELP ! 请求大佬帮助
补充信息
自建了 Derper 并屏蔽了官方 Derper ,使用官方面板
启用了 ACL ,但是我测试过,关闭 ACL 仍然与上述现象描述一致
- A 、B 设备 ACL tag 为 home-server
- C 设备 ACL tag 为 work-pc
// Example/default ACLs for unrestricted connections. { // Declare static groups of users. Use autogroups for all users or users with a specific role. // "groups": { // "group:example": ["[email protected]", "[email protected]"], // }, // Define the tags which can be applied to devices and by which users. "tagOwners": { "tag:home-pc": ["autogroup:admin"], "tag:home-server": ["autogroup:admin"], "tag:work-pc": ["autogroup:admin"], "tag:game-server": ["autogroup:admin"], "tag:game-player": ["autogroup:admin"], "tag:relay-node": ["autogroup:admin"], "tag:out-user": ["autogroup:admin"], }, // Define access control lists for users, groups, autogroups, tags, // Tailscale IP addresses, and subnet ranges. "acls": [ // Allow all connections. // Comment this section out if you want to define specific restrictions. // {"action": "accept", "src": ["*"], "dst": ["*:*"]}, // 允许 out-user 之间全互联 { "action": "accept", "src": ["tag:out-user"], "dst": ["tag:out-user:*"], }, // 允许 out-user 和 game-server 互相访问 { "action": "accept", "src": ["tag:out-user"], "dst": ["tag:game-server:*"], }, { "action": "accept", "src": ["tag:game-server"], "dst": ["tag:out-user:*"], }, // 允许 home-pc 和 out-user 互相访问 { "action": "accept", "src": ["tag:home-pc"], "dst": ["tag:out-user:*"], }, { "action": "accept", "src": ["tag:out-user"], "dst": ["tag:home-pc:*"], }, // 允许其他 tag 之间全互联 { "action": "accept", "src": [ "tag:home-pc", "tag:home-server", "tag:work-pc", "tag:game-server", "tag:game-player", "tag:relay-node", ], "dst": ["*:*"], }, ], // Define users and devices that can use Tailscale SSH. "ssh": [ // Allow all users to SSH into their own devices in check mode. // Comment this section out if you want to define specific restrictions. { "action": "check", "src": ["autogroup:member"], "dst": ["autogroup:self"], "users": ["autogroup:nonroot", "root"], }, ], "derpMap": { // OmitDefaultRegions 用来忽略官方的中继节点 "OmitDefaultRegions": true, "Regions": { "905": { "RegionID": 905, "RegionCode": "cd", "RegionName": "", "Nodes": [ { "Name": "905", "RegionID": 905, "HostName": "", "DERPPort": , "STUNPort": , }, ], }, }, }, } 1 lnbiuc OP 自己回下自己,OpenWRT 防火墙开启 Lan => Tailscale 的 IP 动态伪装即可解决问题 问题解决了,但是没明白原理,还是希望有大佬解答下 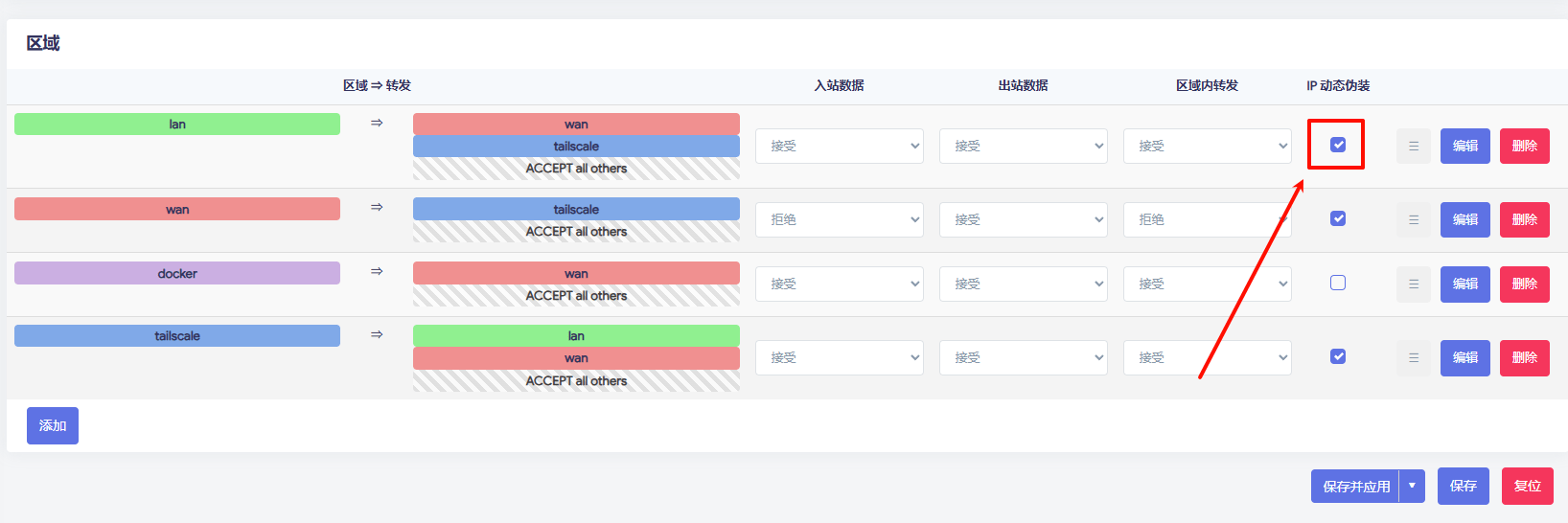 |
